L2TP tutorial
The use of secure protocols on the Internet is one of the most important issues in the field of communication. One of the most secure protocols in this field is the L2TP protocol . For this reason, learning and teaching L2TP is of great importance, and due to the ever-increasing expansion of network issues and remote communication issues, it is necessary to use a number of secure protocols in the Internet network.
In fact, high security and advanced encryptions in the field of protocols should be of great importance in order to be able to communicate and send information at a suitable speed from any geographical point. In this article, we are going to fully examine the L2TP protocol and its advantages and disadvantages, and we will provide explanations regarding L2TP training and the launch of this protocol; So stay with us until the end of the article.
What is L2TP ?
Before the full review of L2TP training, it is necessary to provide explanations about the L2TP protocol and understand what this protocol is and what it is used for. The L2TP protocol is actually a layer tunneling protocol that can be used to fully support VPN services. In fact, Internet service providers can use this tunneling to support VPN. Needless to say, L2TP does not do any encryption on your data and your content and is only used for communication on the VPN platform.
Because L2TP does not have any special authentication and encryption process, IPsec protocol will be used to increase its security and perform the encryption process. In fact, IPsec can encrypt between L2TP endpoints. Some VPNs also use this protocol to provide service and it is several years old.
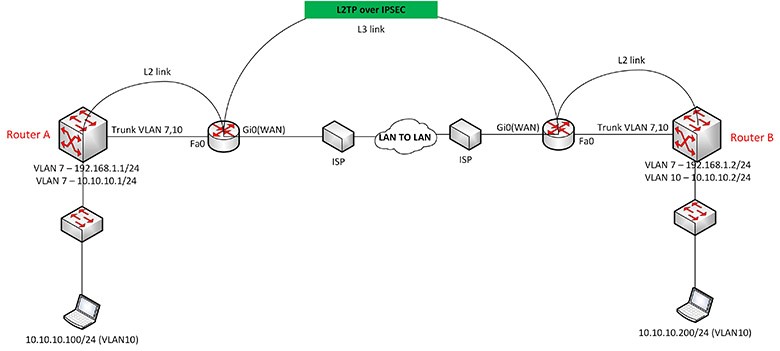
Application of L2TP in the network
In order to know what L2TP training is and how it is, we must first familiarize ourselves with its application. In fact, the use of L2TP in computer networks is often used for network support, and this communication and support occurs in a secure platform and it will not make a difference in what geographical area it is used. Therefore, there will be no restrictions regarding the connection distance
On the other hand, this protocol allows the users of a set to remotely work in a safe and specific environment and only people who are in a set of networks can see the data and contents and the possibility They can be changed or edited for network users.
Advantages of L2TP
Using the L2TP protocol can have advantages. This is why L2TP is so popular and so many users use it; Therefore, before teaching it and building a protocol in this field, we will examine the advantages of L2TP:
L2TP security
One of the important advantages of using L2TP is its security. In fact, L2TP does not show any vulnerability in terms of information leakage, and its encryption, which is done by IPsec, is of 256-bit type. This type of encryption makes it impossible for other people to leak information or access the geographic location.
High compatibility
Another advantage of using the L2TP protocol is its compatibility with various platforms. Also, in order to use L2TP, there is no need to install a special software in different operating systems and you can easily start using L2TP.
Very easy to set up
In the L2TP training section, we will say that setting up the L2TP protocol will be easier and simpler than other VPN protocols. The reason for this is because of its full support for different operating systems. On the other hand, security settings such as Firewall are also very simple and can be set up easily. It is also very easy to switch protocols in L2TP.
L2TP tutorial
Now that we are familiar with the L2TP protocol and its advantages, we will teach this protocol. Since the majority of L2TP usage is on smart phones, here we will discuss how to set up L2TP on Android phones:
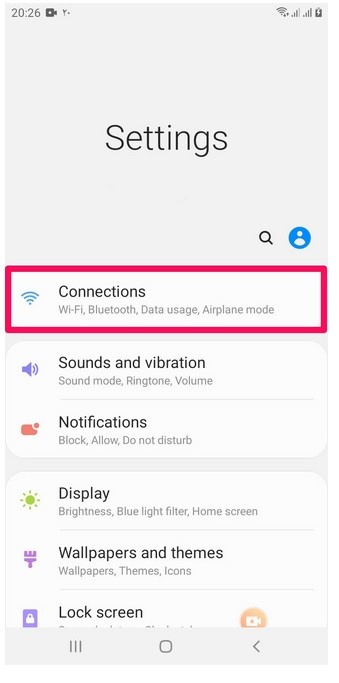
At the beginning of the work, you need to enter the phone settings and select the Connection section.
Then we will enter the More Connection Settings section in the settings and go through the next steps.
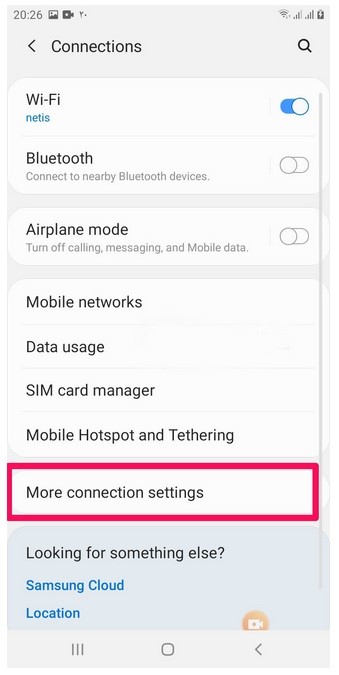
After entering the More Connection Settings section, we will go to the VPN section and apply some settings.
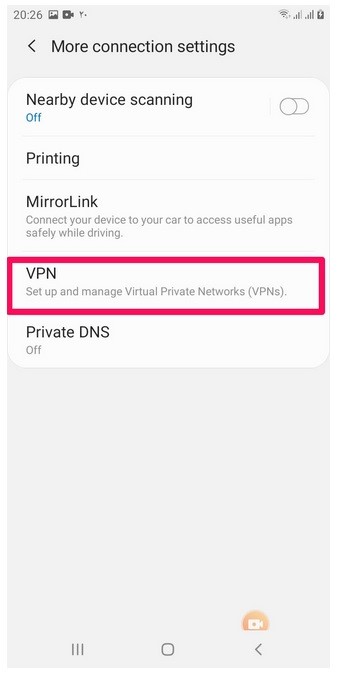
By entering the VPN section, we click the three dots option on the top of the right image.
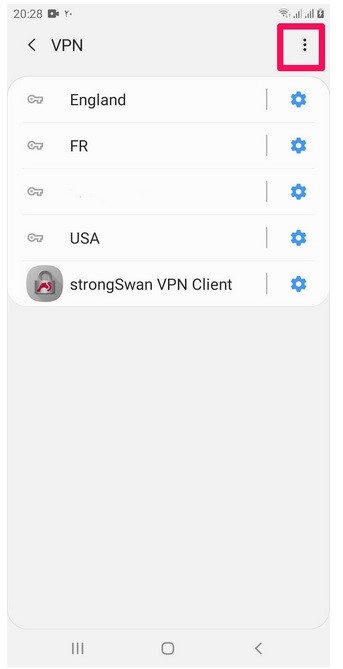
Then we will click on the Add VPN Profile option to enter the main settings.
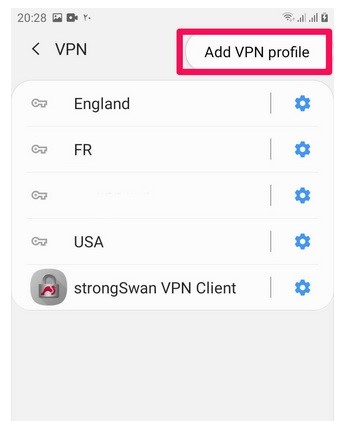
After entering the above settings, we will click the Save option and then connect.
As you can see, we were able to set up the L2TP protocol easily and we can use it well. You can refer to other articles on this site to set up L2TP in other operating systems and make sufficient use of its contents.

Disadvantages of L2TP
Along with the advantages of using L2TP, this protocol can have disadvantages that are worth knowing. It is necessary to provide an explanation. Among the disadvantages of L2TP, the following can be mentioned:
L2TP protocol speed
Due to the increased encryption process in L2TP and re-encapsulation of information, its connection speed may decrease; Therefore, it is necessary to use protocols such as Open VPN to increase the speed in L2TP so that we do not see the speed drop and we can use it easily.
Mismatch regarding security and encryption keys
The L2TP protocol actually uses two-way authentication for its encryption and authentication. This causes L2TP communication to be completely disconnected if both parties do not use the same security key.
Limitations on communication ports
The ports used in the L2TP protocol are limited. The same issue can cause the ports to be blocked and ultimately the L2TP protocol to be blocked in a connection.
Information Leakage
Although L2TP has a good encryption and authentication process, it is still possible for professional hackers to eavesdrop on information and data, and the information is in the hands of other people. This is why L2TP can be compromised by some malware.
cracking
Some research and studies show that L2TP can be weakened or cracked by the NSA after some time. This cracking can increase the damage to the encryption security of the L2TP protocol and compromise its security.

History of the L2TP protocol
The L2TP protocol, or layer 2 tunneling protocol, has been developed since 2000. This protocol was proposed as an RFC standard this year. The roots of L2TP are actually two old protocols for tunneling through point-to-point communication. Over time, with the development of communication and network technology, protocols such as Cisco Layer 2 or L2F and another protocol called PPTP established a newer version related to L2TP. In fact, updating and creating new protocols related to L2TP has added more security features to L2TP and increased its security. Also, the L2TP protocol can switch with the other mentioned protocols in a fraction of a second, and data encapsulation will be done quickly.
One of the important things about L2TP is that unlimited communication occurs in any geographical area and this is considered an advantage. Over time and with the expansion of technology and network, naturally, using the L2TP protocol along with other protocols can make users communicate more easily and quickly in a secure platform.
How does the L2TP protocol work after L2TP training?
After the L2TP process and setting up this protocol in different operating systems, we must have information to use it and its work. When we use L2TP to send a series of data, a general link will be formed for two-way communication. This connection is initially a PPP connection established by your computer or phone with the end user and the service company. On the other hand, two-way communication of PPP type will be established with the service provider and the end user.
On the side of the primary user or the user that sends data, a LAC will be formed to establish PPP to the destination operating system, and in fact, this will make the final connection easily formed. Now, a question may arise, what is the main task of LAC?
In fact, LAC is responsible for forming a security tunnel along with authentication for secure communication in the L2TP platform, which can organize the formed communication in a completely secure and encrypted platform. This is the reason why in such a process, of course, depending on the speed of the Internet, there may be disturbances in terms of work speed.
In fact, the main use of L2TP is to create a secure tunnel between two points on the network platform, where confidentiality of information is the priority of this protocol.
L2TP use cases and performance
Some of the most important uses of the L2TP protocol include:
- Support for L2TP services is implemented as a configuration protocol for VPN services.
- Full support for services related to setting up a personal VPN in a secure platform for a specific connection in a specific network.
- Providing delivery services for internet service providers. In fact, this protocol uses IP addresses of service providers to transfer user information from one place to another.
- Full connectivity to local networks as well as easy remote communication are other features of L2TP.
L2TP protocol agreement
L2TP protocol will encrypt L2TP using IPsec protocol. In fact, L2TP has components including contracts. The service contracts are in the secure platform and in the form of two main contracts ESP and AH. These contracts can do important things such as data access control, authentication of users, confidentiality of user information and even encryption of the type of Internet traffic.
Important features of the L2TP protocol agreement
- L2TP/IPSec protocol uses 3DES or AES encryption method for encryption.
- One of the important features of the L2TP contract is the use of a new encryption method, namely DES 3 or AES, which is remarkable in its own way.
- L2TP protocol has lower speed for tunneling compared to protocols like Open VPN.
- Another important feature of the L2TP protocol agreement is that L2TP is an advanced protocol in the field of VPN, which, of course, requires a lot of effort regarding its security and increasing its security.
- Perhaps the downside of L2TP is that it can be easily filtered and blocked. Because this protocol uses fixed ports.
- Layer 2 tunneling contract cannot be considered a stable contract due to its many complications.
- The L2TP protocol contract cannot be considered as a stable contract due to its complexities.


