Virtual server for your business
dedicated and virtual servers. What are the differences between these two servers? Which of these servers will bring more benefits to the business? Stay with us in the rest of this article to get to know the efficiency of the virtual server for your business and its countless benefits.
Getting to know the virtual server for your business
This server, also known as VPS, is a part of a dedicated server. All businesses need promotion to grow and expand further. For this reason, they should have instant, safe and high-efficiency service. Also, the desired service must give the user the necessary access.
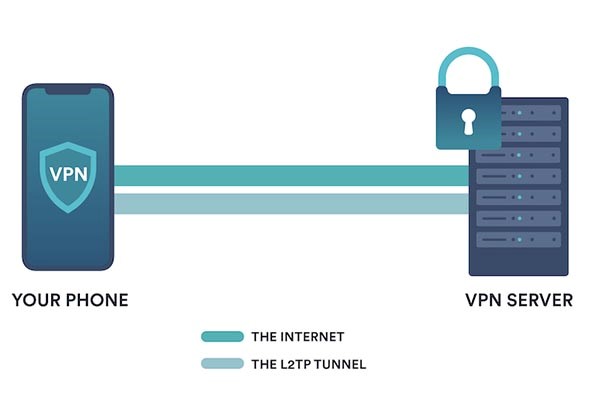
A virtual server is a type of web server that shares computer resources with virtual servers. For this reason, it is not considered a dedicated server independently. In other words, using a virtual server does not make the computer belong to a server software. In fact, this resource is divided between two or more servers separately.
In other words, a server can be considered an always-on computer or system. This system is ready to respond to users 24/7. Also, in the conditions of increased site traffic, it makes your website load faster.
What are the benefits of using a virtual server for your business?
By using this server in the shortest possible time, you will see extensive changes. In addition to increasing productivity, the use of VPS also increases the level of security. In the following, we will examine some of the most important advantages of these servers.
It increases business productivity
As we mentioned, using a virtual server increases the speed. This advantage is due to the simultaneous execution of several processes. The speed of using the Internet and the virtual world in general today has an extremely high position. Also, speed plays a significant role in increasing the ranking in Google. All these things increase the efficiency and productivity of your activities in business.
Reduces additional costs
Buying a virtual server for your business will not cost much. Although you can have a dedicated server at a higher cost, you will probably face a loss in the long run. On the other hand, according to today’s needs of businesses, shared hosting is not very efficient despite the lower price. The virtual server brings more savings and better performance for businesses. It also does not require heavy capital and additional costs.
Increases business security
With the anticipated web security measures activated and implemented by experts, the servers are protected against all kinds of traffic fluctuations, destructive codes, etc. In this way, you will be safe from cyber attacks and you will do your activities with complete security.
Increases flexibility
You can have more resources by using a virtual server. As you know, with the passage of time and business growth, you will need more space to store information. For this reason, by using VPS, you can easily upgrade your RAM space in the fastest time. Of course, this possibility is also available in shared hosting, but it is limited. However, a virtual server allows your business to scale without limits.
It gives freedom of action in choosing the software
By using a virtual server, it is possible to install different operating systems, such as Linux and Windows. In this way, the management and control of the server is provided to the user and you can choose the facilities you want; An important feature that is not available in shared hosting.

Checking the domain term in the virtual server
All sites need a domain to design and run. Basically, after determining the goal and planning for website design, the next step will be domain registration. It can be said that the domain is actually your profile and internet address. Users can find your site easily with the help of this name and address.
The domain consists of two parts, name and extension, and there are no special restrictions for choosing a name. However, the choice of extension has limitations. In fact, the extension specifies the type of site; For example, the extension ORG is used for various organizations and bodies. In this way, the domain can be considered unique to you. Also, keep in mind that the purchase and registration of these domains has a time limit and after its completion and non-renewal, it will be assigned to another site.
Examining hosting terms in virtual server
Host actually means a host that refers to the location of information. The space where you place your site on the Internet will be your host. In this case, you need a device to display your site information to users on the Internet 24/7. This device is called a server, which can be dedicated or virtual. Virtual server has more benefits for your business. However, choosing the type of hosting or server depends on the type of site and your facilities.
Using a virtual server for hosting services is much more popular among users. These servers provide adequate space and volume for your website information at a much lower cost than dedicated servers.

Review some important points before purchasing a virtual server for your business
After getting to know the concept of this server and the advantages of using it, it is time to check some important points before buying a virtual server. In the following, we will examine some important points about purchasing virtual servers.
1. Choose a suitable location with your own virtual server
Before getting a virtual server, it is better to clearly define your goals and needs. In fact, you should know what you are buying a virtual server to do. This helps a lot to choose an virtual server. Each of these servers has its own performance and advantages. You can buy according to these advantages.
2. The virtual server must have proper support
Most of the companies that provide a virtual server for your business have the possibility of support. However, the quality of support is of utmost importance. The provider company must respond to your needs in the fastest time and in the best way. In this way, you can solve the problems as soon as possible. On the other hand, be careful that the company providing the server must have an electronic symbol.
3. Pay attention to the quality of virtual server hardware
The presence of high-quality virtual server hardware for your business also increases the speed. For example, the hard drive of the server has a great impact on the speed; Therefore, it is better to choose it from the SSD type. In general, try to use up-to-date hardware. This will increase the speed of your virtual server. Usually, companies provide you with virtual server hardware information through the support team.
Choosing the right company to buy a virtual server for your business
As we mentioned, many companies are active in this field. Choosing the right host, domain and server requires a high level of specialized knowledge. For this reason, it is very important for internet business owners to choose the right and reliable company to receive these services.
Before buying a virtual server, be sure to pay attention to the company’s trust marks. Many companies do these specialized activities without having enough expertise. For this reason, it is better to be more careful and sensitive in this field.
final word
Buying a virtual server has many advantages for your business. These servers are much less expensive than dedicated servers. However, they also have high quality and speed. Also, by using a virtual server, the security of your data will be much higher. In this way, you will be relieved about cyber attacks, web fluctuations, etc. On the other hand, the virtual server will significantly increase the productivity of your business. These servers have the ability to perform several processes at the same time.